According to a Coalition Report, 79% of small businesses have faced at least one cyber attack in the past five years. Your network may seem quiet, stable, and even, but beneath the surface, hidden vulnerabilities are waiting to be exploited.
Firewalls and antivirus software offer a layer of protection, but they’re not impenetrable. Threats slip through outdated software, unpatched servers, misconfigured devices, and forgotten access points. These cracks don’t just invite trouble; they guarantee it.
“Cybersecurity isn’t the absence of threats. It’s the presence of resilience.”
Sandip Patel, Managing Partner, CISO, and President, Verdant TCS
Every missed update, every exposed port, every overlooked credential is a potential doorway for attackers. And once inside, the damage is swift: stolen data, frozen systems, lost revenue, and shattered trust. The cost is operational, financial, and reputational.
In this guide, you’ll uncover:
- The most common types of network vulnerabilities
- How attackers exploit these weaknesses
- Practical steps to identify, patch, and prevent threats before they strike
Your network is the backbone of your business. Ensure it’s not also your biggest liability.
Top 3 Common Network Vulnerabilities Businesses Overlook
Even in well-managed IT environments, hidden weaknesses lurk beneath the surface. These vulnerabilities often go unnoticed until they’re exploited, turning routine operations into costly disasters.
Identifying and addressing them early is the foundation of strong network security. Let's look at some common network vulnerabilities.
1. Misconfigured Firewalls and Routers
Firewalls are your network’s gatekeepers, but a single misconfigured rule can act like an unlocked door.
Attackers exploit weak or overly permissive settings to access sensitive data, spread malware, or move laterally across systems. Every unchecked rule is a potential breach point.
2. Outdated Software and Unpatched Systems
In 70% of cases, attackers gained entry by exploiting unpatched vulnerabilities, exposing the danger of outdated systems.
Software that isn’t regularly updated becomes a liability.
Hackers actively scan for known vulnerabilities in outdated versions to inject malware or ransomware.
3. Weak Passwords and Poor Access Control
Passwords remain the first line of defense, yet weak, reused, or default credentials are still common. Attackers use automated credential-stuffing tools to break in. Without proper access controls, a single compromised account can give them free rein across your network.
Even small vulnerabilities like these can cascade into catastrophic incidents. Recognizing them early is essential. It saves time, protects revenue, and preserves the trust your business depends on.
See the Threats You’ve Been Missing!
Identify, assess, and eliminate vulnerabilities before they make headlines.
Learn MoreTop Types of Attacks in Network Security That Exploit Vulnerabilities
Your network is a target, 24/7. Attackers don’t wait for permission; they probe, adapt, and evolve. Their methods are designed to exploit the smallest cracks in your infrastructure, turning overlooked vulnerabilities into full-blown breaches.
Here are four common network attacks to look out for:
1. Malware: Trojans, Ransomware, Spyware, Adware
Malware is relentless. Trojans pose as legitimate apps to sneak in unnoticed. Ransomware locks your data and demands payment. Spyware monitors user activity in the background, while adware drains system resources and slows productivity. These threats exploit outdated software, weak configurations, and human error.
2. Phishing and Social Engineering Attacks
Every day, 3.4 billion phishing emails flood inboxes, making up 1.2% of total global email traffic. Attackers use email, SMS, and voice calls to manipulate employees into revealing sensitive information. AI-generated phishing emails now mimic trusted sources with alarming accuracy. One click, one reply, and attackers gain access to credentials, systems, or financial data.
3. SQL Injection and Cross-Site Scripting (XSS)
Poorly coded web applications are easy prey. Malicious input can manipulate databases, extract confidential data, inject malware, or disrupt operations. These attacks thrive on weak input validation and a lack of secure coding practices.
4. Distributed Denial of Service (DDoS)
DDoS attacks flood your servers with traffic until they crash. Often paired with malware for maximum chaos, these attacks exploit infrastructure weaknesses and overwhelm systems. Without real-time monitoring, your network can go dark in minutes.
Prevention starts with visibility: identifying gaps, patching weaknesses, and training your team to recognize threats before they strike.
Hidden Cyber Vulnerabilities Inside Your Network
Not all threats come from the outside. Some of the most dangerous cyber vulnerabilities are buried deep within your organization, quiet, overlooked, and waiting to be exploited. These internal risks often bypass traditional defenses and can be just as damaging as external attacks.
1. Insider Threats and Human Errors
65% of breaches stem from outsiders, while 35% are caused by employees, often due to unintentional errors. Employees can unintentionally expose systems by mishandling sensitive data, clicking on phishing links, or misconfiguring devices.
Worse, malicious insiders may deliberately exploit their access to steal information or sabotage operations. Continuous monitoring and strict internal policies are essential to detect and deter both.
2. Shadow IT and Unauthorized Devices
Unapproved apps, rogue software, and personal devices often connect to networks without IT’s knowledge. These hidden nodes bypass security protocols, creating blind spots that attackers can exploit. Without visibility and control, your network becomes a patchwork of unknown risks.
3. IoT Devices and Endpoints
Smart thermostats, printers, and remote laptops may seem harmless, but they often lack proper security settings. Attackers target these endpoints to gain entry into larger systems. Regular audits and full visibility into every connected device are critical for early detection and containment.
Continuous assessment, device visibility, and internal vigilance ensure you identify and neutralize these unseen gaps before attackers do.
| Read this next: |
How to Detect Network and Information Security Vulnerabilities
Detection is half the battle, but it’s the half that determines whether you catch threats early or clean up after disaster. Network vulnerabilities don’t always announce themselves. They hide in system logs, user behavior, and outdated configurations. Proactively identifying these weak points is the difference between resilience and regret.
1. Continuous Monitoring and Logging
Every device, connection, and system behavior should be tracked in real time. Unusual activity, such as unexpected traffic spikes or login attempts, can signal exploitation. Logs also serve as forensic goldmines during investigations and help meet compliance standards.
2. Vulnerability Scanning and Penetration Testing
Automated scans reveal software flaws and misconfigurations. Penetration testing goes further, simulating real-world attacks to expose weaknesses that scanners might miss. Together, they offer a comprehensive view of your network’s soft spots.
3. Behavioral Analytics and AI-Based Threat Detection
Advanced tools analyze user and network behavior, flagging anomalies that traditional systems overlook. AI can detect subtle patterns, such as lateral movement or privilege escalation, giving your team time to respond before damage is done.
Reducing Risks from Network Security Vulnerabilities
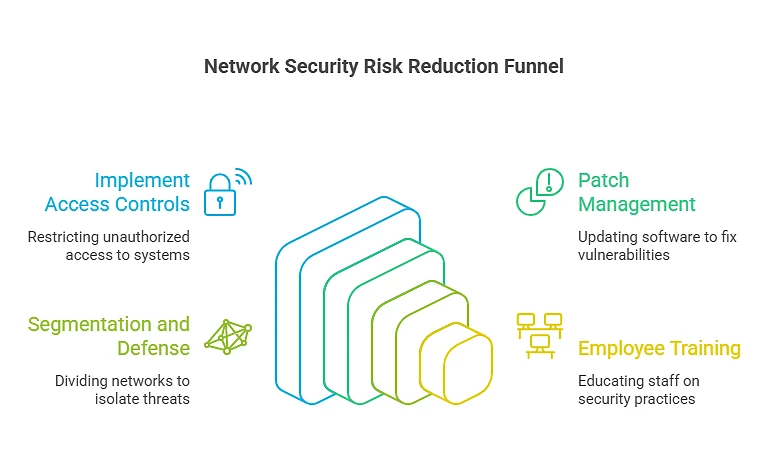
Being vigilant in detection ensures that even subtle vulnerabilities are addressed before they escalate. But detection alone isn’t enough. Reducing risk requires strategic action.
- Implement Access Controls and MFA: Limit access based on roles and enforce multi-factor authentication. Even if credentials are compromised, layered defenses prevent unauthorized entry.
- Patch Management and Software Updates: Frequent updates close known gaps. Automated patching reduces human error and ensures systems stay protected against emerging threats.
- Segmentation and Perimeter Defense: Divide your network into zones to contain breaches. Firewalls, VPNs, and strict access policies create barriers that slow attackers and protect critical assets.
- Employee Training and Security Awareness: Your team is your first line of defense. Educate them on phishing, unsafe downloads, and social engineering tactics. A well-trained staff can stop attacks before they start.
Emerging Cyber Threats and Vulnerabilities to Watch
Cyber attackers constantly refine their tactics, leveraging new technologies and exploiting overlooked gaps. Staying ahead of new types of network security threats means knowing what’s coming and adapting your defenses before the next breach. Here are four major trends to look out for:
- Generative AI-Based Attacks: AI now empowers attackers to craft eerily convincing phishing emails and social engineering schemes. These messages mimic tone, branding, and timing so well that even trained employees can be fooled.
- Supply Chain Vulnerabilities: Your security is only as strong as your weakest vendor. Third-party software and services can become Trojan horses, giving attackers indirect access to your network. Vetting partners and monitoring integrations is survival.
- Zero-Day Exploits: These are the ghosts in the machine, undiscovered flaws that attackers race to exploit before developers can patch them. Rapid response capabilities and advanced detection tools are critical to staying ahead.
- Account Takeovers and BEC Scams: Attackers hijack user accounts or impersonate executives to commit fraud, redirect payments, or steal sensitive data. Strict verification protocols and behavioral monitoring can prevent these scams.
Consequences of Ignoring Network Vulnerabilities
Ignoring network vulnerabilities is an active risk. The cost of inaction is steep, and it hits where it hurts most: your bottom line, your operations, and your reputation.
- Financial Loss and Operational Disruption: Data theft, ransomware, and system outages grind productivity to a halt. Revenue drops, recovery costs spike, and business continuity suffers.
- Reputational Damage: Public breaches erode customer trust. Once lost, that trust takes months or years to rebuild. In competitive markets, reputation is currency.
In 2023, a major breach struck the MOVEit Managed File Transfer system. Hackers exploited a critical network vulnerability, an SQL injection flaw, to infiltrate public servers and deploy a web shell that stole sensitive files.
The attack spread rapidly through organizations relying on MOVEit, compromising government agencies, corporations, and millions of individuals worldwide. The incident exposed data from over 2,500 organizations and affected roughly 93 million people. It was a stark reminder that a single unpatched vulnerability in one network-connected platform can cascade across entire industries.
Overlooked Network Vulnerabilities and Protective Measures
The table below highlights lesser-discussed vulnerabilities and actionable measures to protect against them.
| Vulnerability Type | Description | Recommended Actions |
| Misconfigured DNS Settings | Incorrect DNS records redirect traffic or expose data | Regular DNS audits, DNSSEC implementation |
| Legacy Protocols | Outdated communication protocols create exploitable channels | Disable old protocols, enforce secure alternatives |
| Unencrypted Backups | Stored data is accessible if devices are stolen | Encrypt backups, enforce strict access controls |
| Cloud Misconfigurations | Improper cloud storage settings expose sensitive files | Regular configuration reviews, CASB tools |
| Forgotten Devices on the Network | Unused hardware remains connected, potentially unpatched | Routine asset inventory, disable unused devices |
| Physical Network Access Weakness | Unauthorized personnel can access server rooms | Surveillance, badge systems, biometric controls |
Partner with Verdant TCS for Reliable Network Security
Every network contains vulnerabilities waiting to be exploited. You now understand the most common and hidden weaknesses, the attacks that exploit them, and the most effective ways to identify and manage risk.
Verdant TCS, a leading provider of network security solutions, delivers proactive protection backed by proven expertise and integrated cybersecurity capabilities. With a fully integrated 13-layer security stack and round-the-clock threat monitoring through our SOC, we provide enterprise-grade defense without the enterprise complexity.
| Trusted Cybersecurity and IT Services Near You |
With Verdant TCS, you gain more than a security provider; you gain a partner committed to keeping your infrastructure resilient against emerging attacks and hidden vulnerabilities.
Contact us today to schedule a comprehensive vulnerability assessment and take control of your network’s security posture before the next threat hits.



